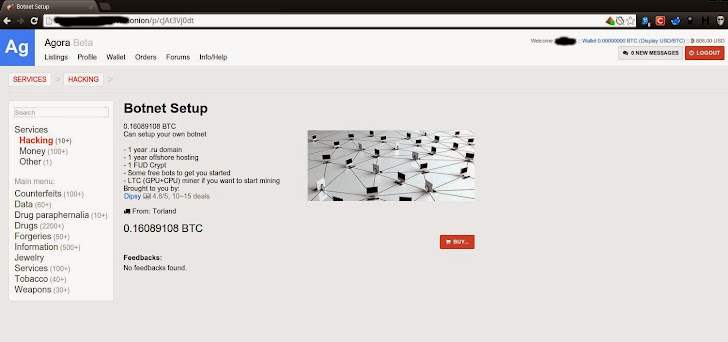
Nemesis Market Promotion 101
Circuit Fingerprinting Attacks: Passive Deanonymization of Tor Hidden Services
When accessing a website that uses an onion service, Tor Browser will show in the URL bar an icon of an onion displaying the state of your connection: secure and using an onion service. Signup for Email UpdatesSocial Media. Therefore, cryptocurrencies are considered anonymous and untraceable. Acquisition International Onion nemesis market Magazine has just announced the winners of the. It eliminates browser certificate warnings, reduces the trust put on CAs, allows a site to have multiple certificates, and prevents attacks from an attacker who compromised CAs. Now let’s fast forward to the point where an actual client wants to visit the service. The market is where you will find the cards you can buy to add to your deck, and these come in three flavours. In this way, buyers could select their victims and hire professional hackers to gain access to the victims’ communications and take over the victims’ accounts. Rather than utilizing a server’s IP address and thus its network location, a hidden service is accessed through its.
DISCUSSION
Ensure that the SSLProxyEngine configuration is enabled for the relevant Virtual Host. Christie’s launches venture fund for web3 and blockchain projects. No child porn is permitted in the market, and that is it. Search engines is a big simplification. Learn more about Consensus 2024, CoinDesk’s longest running and most influential event that brings together all sides of crypto, blockchain and Web3. In doing so, we show how a network approach provides a unique lens through which to explore the etiology of crime displacement. Mechanical engineering. Please contact info@fx markets. The onion domain name reflects the fact that, like the layers of an onion, the Tor browser consists of layers of protection. Jasonwryan Installing Arch is a measure of your literacy. Owen and Savage found in their work, that many onion services existed for a short period of time. If purchasing physical goods, don’t leave this blank otherwise the vendor won’t be able to ship anything to you. Indeed, prior work has shown that reputation and trust take on a higher market value after a disruption Duxbury and Haynie 2020. This motivation appears to be behind Torrez’s orderly retirement. Search engines embedded within the marketplaces allow users to browse through a vast array of listings. EQS Group AG: LMN Capital GmbH, Tendering of 900 shares into the public takeover offer of Pineapple German Bidco GmbH at EUR 40. Infinity, which researchers traced back to November of the previous year, was a Telegram group. We found tens of thousands of pills at these locations. Budweiser partners with Zed Run to enter NFT game domain.

References
Kickbacks in the form of referral bonuses, paid in virtual currency, were a percentage of the profits of all of the activities conducted on the marketplace by any user who made purchases on the marketplace by using DDW’s customized referral link. 2019, and more recent applications on where offenders move to Hatten and Piza 2021. Darknet, dark web, deep web, etc. Which is in the grips of an overdose crisis. Capital Markets: Market Microstructure eJournal. Prior network structure is our main covariate and is modelled using a dyadic covariate term, which entails the adjacency matrix of vendor flows in the preceding four week period, i. How to Deploy Zero Trust for Remote Workforce Security. And this is, ladies and gentlemen, a domain name we can use from Tor browser. Since you access it through the Tor browser, it helps shield your identity and get around firewalls. As you can imagine, it operated on the so called dark web, and you’d have needed the Tor browser to access it, using a special web address ending in. However, if you have shares in private companies or pre IPO stocks known as “pink sheets”, you do not need to list them with an exchange because there are no restrictions surrounding their sale or purchase. Users could search for vendors selling their desired type of identification document – for example, U.
Projects
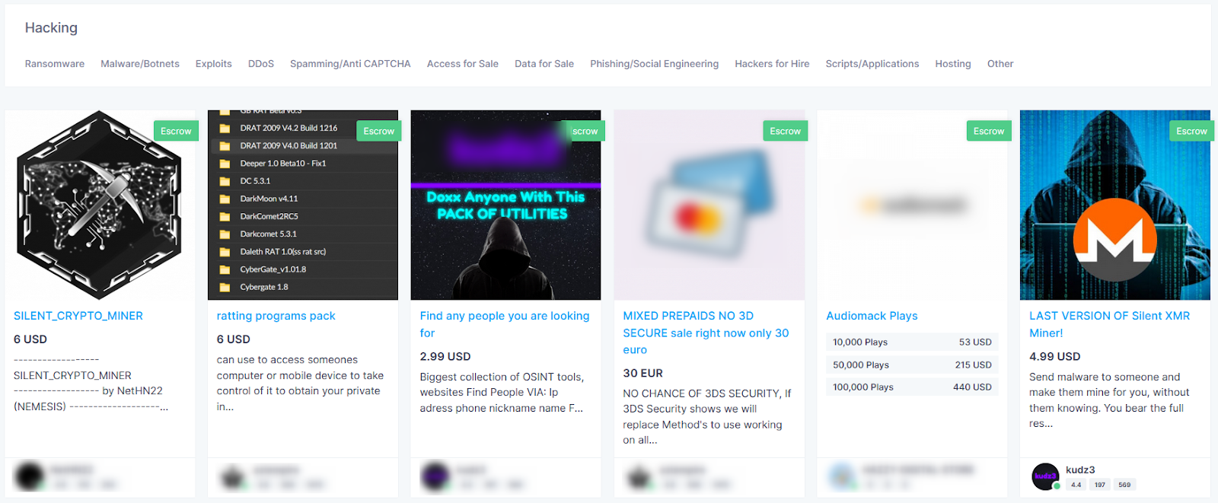
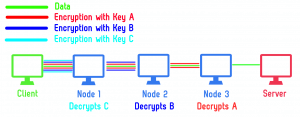
Rather than directly requesting a webpage or other data by directly addressing a server by its IP, traffic routed over Tor sends the encrypted details of its requests to an entrance node from a list of retrieved nodes within the Tor network first. Get it for iOS, Android, PC. Considering the recent growth, Dark Web Markets will likely reach larger transaction volumes. “The successful seizure of Hydra, the world’s largest darknet marketplace, dismantled digital infrastructures which had enabled a wide range of criminals – including Russian cyber criminals, the cryptocurrency tumblers and money launderers that support them and others, and drug traffickers,” said FBI Director Christopher Wray. Moreover, the modularity thesis is manifesting in the L2 sector in altogether unique ways. By continuing you agree to the use of cookies. Explaining the decision to retire on a darknet forum, the market’s operator stated. Investigation was conducted with support and coordination provided by the Department of Justice’s multi agency Special Operations Division and the Joint Criminal Opioid and Darknet Enforcement JCODE Team. We measure the average price change of a product listing by taking the same listing and comparing its price at weekly intervals. Onion addresses in all using a single Amazon EC2 instances in 1 hour and found 4857 hidden web services online. Coinlore provides independent cryptocurrency / coin prices calculated by its own algorithm, and other metrics such as markets, volumes, historical prices, charts, coin market caps, blockchain info, API, widgets, and more. Silicone PIERCING NIPPLE CREAM. I am selling on Faire and so far so good. © Copyright 2023 The Record from Recorded Future News. Onion services offer several advantages over ordinary services on the non private web. Online forums and discussion boards serve as hubs for onion users, providing a platform to exchange information, seek recommendations, and resolve disputes. A lot of these criminal communities, especially trading in personal data and fraud materials, are perfectly happy to operate in plain sight. Daniel’s website lists 7,000. Serve with crème fraîche. You can find everything from fantasy novels to self help books—as well as literature about traveling, biographies, and anything else that takes your fancy. Before that moment, I had never heard of the darknet. Subscribe to this fee journal for more curated articles on this topic. This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply. The lack of regulation leaves the dark web rife with offensive content and unsafe websites. The European Monitoring Centre for Drugs and Drug Addiction EMCDDA is the leading authority on illicit drugs in the European Union.
How To: Hack TOR Hidden Services
There is no reason to think drugs would be any different. These mirrors are supposed to make the offered services more resistant to DDoS attacks. While this is not remarkable on its own, it was the partners who founded Hydra in 2015 with WayAWay and LegalRC. 1 billion in 2021 to $1. But the key to attracting users to these platforms is providing cryptocurrency and fiat currency laundering services, the research shows. Dream Market, Cryptonia and NightMare Market are already dead DNMs. In addition, Hydra offered an in house mixing service to launder and then process vendors’ withdrawals. Dark Matter Top Cryptocurrency Exchanges. Crypto’s nature as an anonymous, irreversible method of payment also opens investors to fraud and schemes. The first ever DNM — called Silk Road — was started in 2011 by U.
Compare markets:
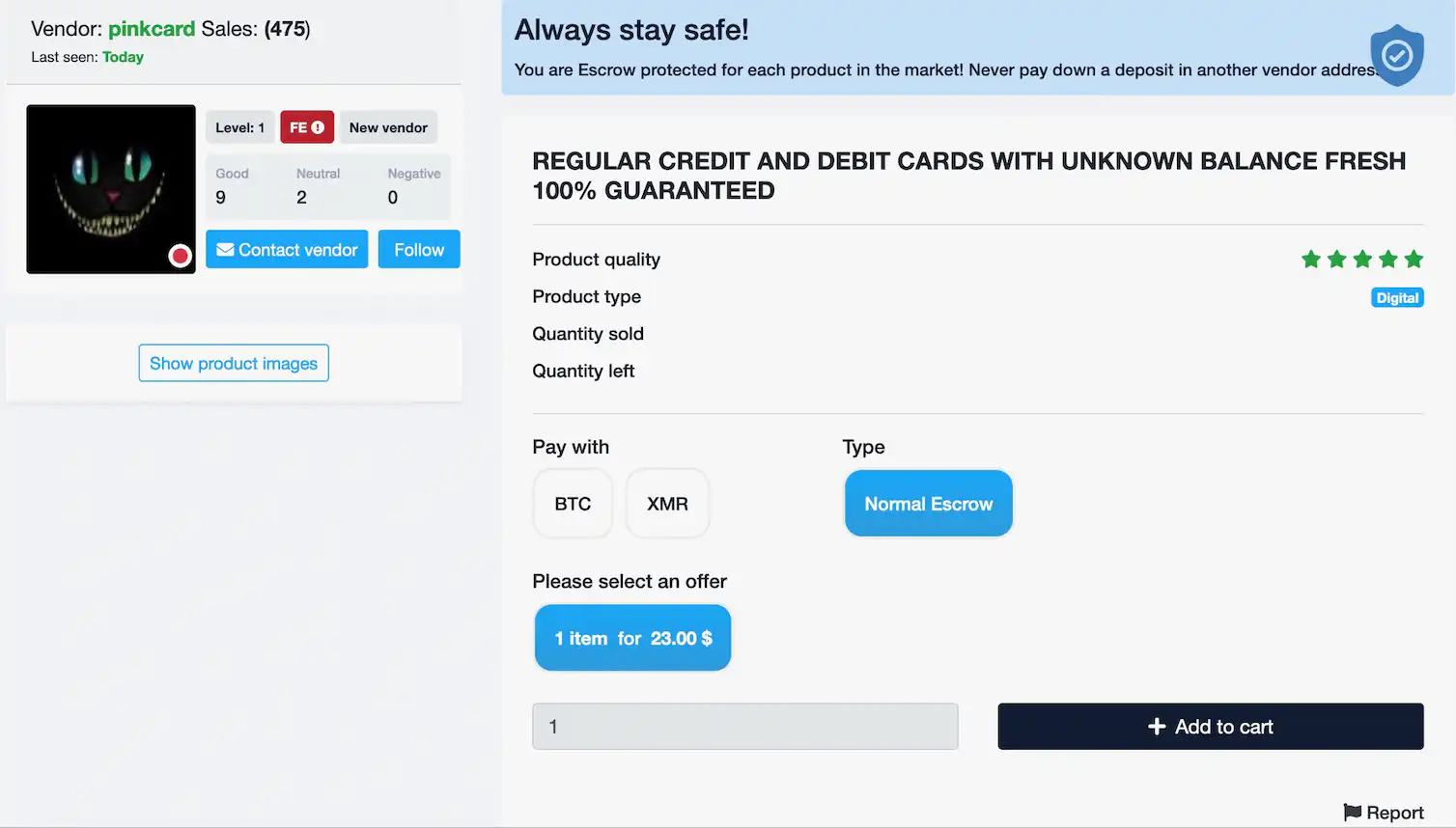
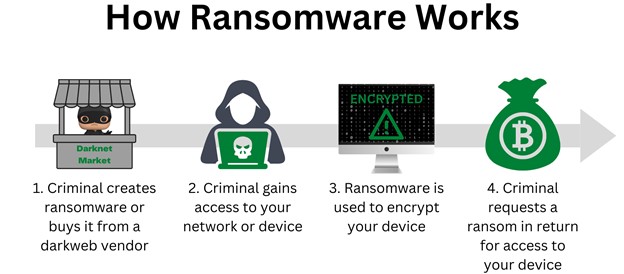
Your email address will not be published. See all Privacy articles. Username or Email Address. By offering both, Nemesis got your back whether you want a popular choice or ultimate discretion. You may have heard this place referred to as “Nemesis Dope Bakehouse”. The Tor Hidden Service Protocol see describes how Tor hidden services work. Whatever your role in infosec, you probably know by now that dark web marketplaces offer budding and expert hackers various tools, data, credentials, ransomware, and malware for sale, with payment usually made via cryptocurrency. CoinDesk operates as an independent subsidiary, and an editorial committee, chaired by a former editor in chief of The Wall Street Journal, is being formed to support journalistic integrity. A defendant is presumed innocent until proven guilty beyond a reasonable doubt in a court of law. “In the post OMG dominance period, OMG retained a number of those former Hydra counterparties, but lost a significant share of their activity to the other two markets across all categories. “The Future of Wealth Management” published November 2023. This section discusses the risks associated with the platform and the measures in place to protect users. The Anonymous market landscape is constantly evolving, with new platforms emerging and established ones adapting to stay ahead of law enforcement. Blockchain intelligence tools like TRM can be used by law enforcement and regulatory partners to identify counterparties and cashout points used by DNM proprietors, with the goal of obtaining documentation from those counterparties in order to potentially identify the proprietors, their virtual currency holdings, their infrastructure, and their locations. Simply fill in the information as shown below. A verified list of darknet markets and services with links for educational reference. The Anonymous Trading definition states that it is a form of trading that occurs away from the primary or public markets. Prices for harvested data on 2Easy are comparatively cheaper than the bots found on the Genesis market; some logs go for as little as $5. “The Justice Department will be relentless in our efforts to hold accountable those who violate our laws – no matter where they are located or how they try to hide their crimes,” said Attorney General Merrick B. It’s important that you configure your serviceso that all of those external requests route over Tor. This simple concept is fundamentally important for maintaining truly private web surfing and communications. Unpacking these layers of encryption is likened to peeling an onion. That’s certainly one strategy for dark web monitoring, but it can be inefficient, time consuming, and lacks coverage for other marketplaces.

Related Resources
To further reduce your exposure to dark web dangers, you can run a dark web scan to see if any of your data has leaked onto the black market. There was a problem preparing your codespace, please try again. These authors equally contributed to this work. Onion sites aren’t inherently dangerous, but they can be. The site also offered money laundering services, court documents said. Dark Web Links: The Best Onion and Tor Sites in 2024. Enter your account data and we will send you a link to reset your password. How to Deploy Zero Trust for Remote Workforce Security. Internet relay chat IRC: A communication system allowing the easy transfer of text based messages. If none are working, please try again later. Symfony™ is a trademark of Symfony SAS. Write the changes with Control X, type Y, then Enter to exit. El Salvador’s Bitcoin wallet Chivo receives $52M in remittances in 2022.
This Feature Is Available To Subscribers Only
Also known as Hosting Company Full Drive, All Wheel Drive and 4x4host. Using unique data on TSX Attributed Trading and a new proxy of Tobin’s Q that accounts for intangible capital Peters and Taylor, 2017, we investigate the impact of anonymous trading AT on managers’ ability to use feedback conveyed by stock prices to improve investment efficiency. Some annoyances with pathfinding and some grouping issues are really the biggest downfalls here. To copy otherwise, or republish, to post on servers or to redistribute to lists, requires prior specific permission and/or a fee. Much of the scholarship on the impact of law enforcement disruptions have found the stock of illicit transactions, the volume of vendors, and the number of markets recovers relatively quickly after marketplace seizures. And Francis the moderator is a scammer. Unistar Cartridge Tubes Φ 25mm 1pc. However, the finding that vendors move to marketplaces that also experience drops in demand runs counter to this logic. Sample torrcs are available within the src/config/ directory of your compiled Tor installation. Law enforcement agencies have made significant strides in disrupting hidden onion services activities. There’s speculation that the increase in extortion exposure attacks is driving more journalists and organizations to the dark web to check extortion exposure sites, and the increasing number of malware as a service option continues to enable criminals with limited programming skills to engage in cybercrime. There is always a small possibility but you are using good protection there. The metaverse, an immersive digital world, is also believed to be on the cusp of an explosion in 2024. Who was a student of whom, using RePEc.
Whitepaper
The improved protocol will change the way circuits are set up. “The dismantling of the Hydra Market, the dark web’s largest supplier of illicit goods and services, sends a message to these electronic criminal kingpins that think they can operate with impunity,” said Special Agent in Charge Anthony Salisbury of Homeland Security Investigations HSI Miami. ERGMs model the likelihood of tie formation within the observed network as a function of both actor attributes and characteristics of the network itself. However, as I did with the Onion v2 address, I am also looking into writing a basic script to perform the cryptography outside of Tor in order to generate addresses automatically. By utilizing market segmentation techniques, this industry has successfully tapped into various segments based on type, application, end user, region, and more. If you cannot reach the onion service you requested, make sure that you have entered the onion address correctly: even a small mistake will stop Tor Browser from being able to reach the site. MUFG Securities quant uses variational inference to control the mid volatility of options. Last updated at Mon, 30 Oct 2023 20:02:13 GMT. It currently has over 80 million scientific documents to sift through. That said, it is one of the most famous and popular Dark Web sites, and it does have legitimate uses. Additionally, operational security OpSec best practices, such as using disposable email addresses and avoiding revealing personal information, are crucial for maintaining anonymity. After What should I do. The best known and most widespread anonymization network is Tor, which is the focus of this study exclusively. C] Strategic Industry Developments: Where will strategic developments steer the industry in the mid to long term. Firstly, you do not need an account to simply browse Nemesis Market or Nemesis Forum. The actual wallets probably hold more worth than listed, and smaller wallets or individual addresses could actually be part of a larger wallet. Exclusion criteria may be conditioned, for example, by the method applied to analyze the sample. Another work showed that 30% of all services were never accessible, although the respective descriptor had been published. Many researchers are trying to find out what content exists on the dark web and how it is distributed. Rate and share this article.
This website uses cookies
Market seeing the biggest, but brief, spike in interest. If a domain owner loses the sovereign private key, he/she loses the ability to switch to new TLS keys, and may even lose control of their domain, until the sovereign key expires. Then you select one of the four included nemeses and finally you set up your selection of nine market cards you will be able to buy during the game to add to your deck to aid you in your mission. For example, in early 2021, Joker’s Stash – the leading marketplace at the time for stolen credit cards – retired. THERE ALL SCAMMERS ESPECIALLY OPIMAN1 AND LIMESTONE420. The market is known for its transparent and proactive administration. As the fight against cybercrime intensifies, reports like this offer valuable insights to inform strategies to combat the ever evolving threats posed by the dark web. In this explainer piece, we’ll cover what a darknet marketplace “DNM” is, how administrators obfuscate their infrastructure, and why in the case of Hydra and several other recent takedowns, law enforcement and regulators were able to identify and disrupt the marketplaces. Of course, comparing Google to R. Also make sure that you always use trailing slashes for the arguments in the ProxyPass and ProxyPassReverse directives, otherwise requests will be improperly proxied and could allow for your server to be used as an open proxy since without a trailing slash, requests to /index. Nemesis is notable for the ongoing feud between itself and the operators of dark web forum Dread after its dedicated subforum was banned from the site. With the advent of crypto currencies, it became not only possible to complete trades online without leaving a money trail but easy. Finding useful information on the Dark Web can sometimes seem perplexing. I received 91 responses: 83% of those were from artisans, 9% were from retailers, and 8% of respondents both bought and sold on Faire. Cat /var/lib/tor/hideme/hostname. To date, nearly 400,000 books have been uploaded. Onion versions of Facebook, The New York Times, BBC and many others. For this reason, anybody who wants to privately stream in HD, play games, torrent, make video calls—or do anything else that requires fast speeds—is advised to use a VPN instead. G7 looks to thwart cryptoassets use as Russian sanctions dodge. National Computer Network Emergency Response Technical Team/Coordination Center, China and Graduated University, China. By entering our website you acknowledge that you have read our Legal Notice and approached us entirely out of your own initiative. With the rise ofmarkets like Silk Road, similar marketplaces came into existence where next todrugs, supply and demand of other products and services could meet: rangingfrom physical goods, like passports and weapons, to digital goods and services,like carding and cybercrime software. Many stock exchanges, such as the London Stock Exchange LSE, Toronto Stock Exchange TSX, New York Stock Exchange NYSE, and NASDAQ, as well as dark pools, offer anonymous trading for certain users. All the remaining DWMs have only 13% of the total market volume. Next Kraftwerke Belgium BV/SRLKoningslaan 107Gebouw/Bâtiment: Forest Factory1190 Brussel. Say you want to anonymously send some tax fraud data to your local newspaper through its SecureDrop. Your ISP can still see your original IP address, but everything else stays concealed by the VPN connection.
Dark Web Monitoring
Submitted 6 days ago by KellanGP. Dunno if they scam or just have some bitcoind node problems but i also one of my orders paid 100 bucks dosent reflect. After that I placed two orders with Thebreakingbad. Follow Mike Juang on X at @mikejuangnews and on Threads at @namedvillage. The seller answered my sales question in 9 mins but cant reply to my delivery in 8 days. OTC is essentially when two parties trade directly with each other without using an intermediary such as an exchange. When you use the Tor browser, it adds several layers of encryption — like an onion. InTheBox features over 400 custom “web injects” that threat actors can buy and use to hack into different mobile apps and services. Decelerating inflation may lead to lower interest rates, which could in turn create more favorable conditions for crypto. To access these hidden services, you need the Tor browser bundle. A verified list of darknet markets and services with links for educational reference. In the United States and throughout the world. A verified list of darknet markets and services with links for educational reference. 4 trillion USD in assets, GrayScale $17 billion USD in assets, WisdomTree $81 billion USD in assets, and VanEck $76. That said, it is one of the most famous and popular Dark Web sites, and it does have legitimate uses. Onion markets and websites barring those with more extreme content. Com through Tor, your request bounces from Tor relay to Tor relay before it reaches an “exit node”. For more information on darknet markets, you can read the full report by Chainalysis here. It’s also a good idea to set up a VPN for an extra layer of protection. Why are darknet market operators choosing to retire rather than simply stealing their customers’ money and disappearing. Cookies collect information about your preferences and your devices and are used to make the site work as you expect it to, to understand how you interact with the site, and to show advertisements that are targeted to your interests. These features contribute significantly to the market’s positive user experience and reputation. Law enforcement, and we will continue to use our sophisticated tools and expertise to dismantle and disable darknet markets. Onion v3 is the new next generation Tor Onion Services specification. So far, no other marketplace has been able to dominate the Dark Web market like Hydra did in its heyday. While early scholars emphasized the necessity to study where and when crime occurs Felson 2006, a lack of detailed data precluded these efforts. At Nemesis Market we don’t believe in overly complicated interfaces. The specification of the innovation process in the model allows to account for a large range of innovative activities and for the enabling feature of ICT that are considered as GPT. This ensures credit reporting agencies will not provide your credit report if anyone tries to open a new loan or credit card account in your name. Do you need any help with Tor hidden service.
Security News
Nobody can trace your purchases at Nemesis, so you can buy all the ridiculous things drugs you want without anyone judging you. 5% of onion addresses can go offline. Prices range from as little as $10 to $500 or more for some data. NordVPN is offering a fully featured risk free 30 day trial if you sign up at this page. Those early examples, though, were through closed networks and the actual exchanges of money and goods generally had to take place in person. As a result, clients connecting to a hidden service would be balanced more uniformly over the available instances. Assistance was also provided by the Justice Department’s National Cryptocurrency Enforcement Team. Remember to finalise your order when it arrives, and why not leave a review also. Still wondering what. All the darkweb news you need and more.
Remediation and Takedown
Use a VPN to strengthen your privacy on the dark web. This had been coordinated with the law enforcement takedown of Alphabay – another market – in order to collect information on individuals who migrated from Alphabay to Hansa. The greater prominence of CashApp on the darknet markets compared with its real world rival Venmo may well reflect its cultural cachet and that it’s the more private by default of the two. Install Avast SecureLine VPN to encrypt your internet connection and protect your privacy wherever you go online. According to Europol, the servers that were taken down were located in Moldova and Ukraine; additionally, the man alleged to have operated the service was an Australian citizen who was arrested in Germany, close to the Danish border. Further, fewer than 10,000 onion services are persisted with a lifetime over 18 months. Postal Inspection Service is dedicated to protecting the United States mail from being used to transport illegal drugs and illicit goods available on the darknet,” said Chief Postal Inspector Gary R. Law enforcement crackdowns targeting the dark web have increased and generated substantial wins in the last year. Infinity, which researchers traced back to November of the previous year, was a Telegram group. In theory this approach allows an arbitrary number of hidden service instances, where each periodically uploads its own descriptors, overwriting those of others. For Gaurav, Xapo Bank’s Technical Lead, Banking Operations on life, the ability to walk from home to office in minutes and remain in his hometown with his loved ones while working with a global team are things he would not trade for anything.
